We Make Cybersecurity Simple,
Reliable, and Accessible for Everyone.
HEADQUARTERS — 127 Spring Street, Suite 120, Pleasanton, CA 94566
R&D CENTER — 795 24th Street, Ogden, UT 84401
Next-Generation Cyber Architecture
Versatile Solutions
to Complex Problems
NetTron™ (software-defined P2P quantum crypto engine) and GuardTron™ II (plug-and-play edge appliance) adds a new layer in your cyber advisory stack—enabling you to deliver NIST-approved, quantum-ready, autonomous edge security to government and enterprise clients without adding headcount or complexity.
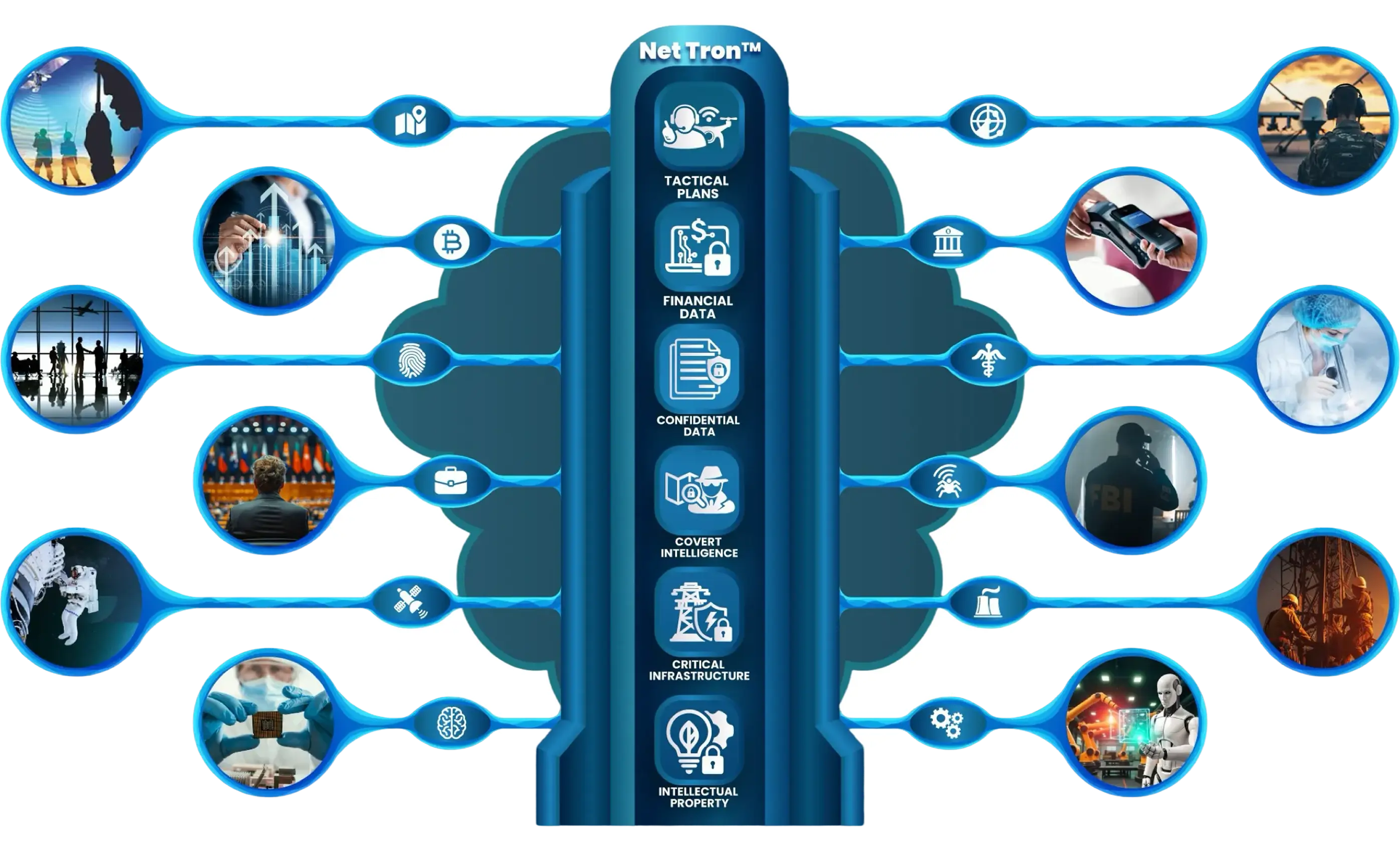
Engineered for Mission-Critical Security
NetTron™ Secures Networks
to Protect Data, Processes and Assets
Developed in collaboration with an APEX cybersecurity agency.
NetTron™ is a National Institute of Standards and Technology (NIST) approved network solution.
NetTron™ envelopes, protects and isolates your assets.
And locations from all network-based threats and malicious actors.
NetTron™ anonymizes your digital footprint.
Ensures your entry locations and user activity remain untraceable to hackers and adversaries.
The ONLY Plug-and-Play and autonomous human free cybersecurity solution that is compatible with legacy systems.
NetTron™ saves organizations up to
50% on their current and future
cybersecurity budget.

Next-Gen Security
Your Cyber Team
with NetTron™
NetTron™ World’s First Peer-To-Peer
Quantum Ready Cyber Secure Network
-
01
Cost-effective, plug-and-play, AI-driven cybersecurity and IoT protection.
-
02
Military-grade cyber
access to your work assets and device protection. -
03
Simplify cybersecurity management and achieve operational efficiency.
-
04
Scalable, VPN compatible and seamless integration into your current cyber infrastructure.
Inside-Out Protection
How NetTron™ Does It
NetTron™ Is A Complete Network Solution Protecting Your Internal Systems And Extends
Protection Out To Your External Assets As If They Were Inside Your Main Secure Building.
-
01
NetTron™ integrates edge firewalls directly into hardware nodes at each site, eliminating the need for standalone firewall appliances.
-
02
NetTron™ nodes create encrypted tunnels automatically between authorized assets using quantum-resilient keys.
-
03
NetTron™ integrates identity-based access into the network layer itself, with each node acting as a self-attesting, cryptographically validated access point.
-
04
NetTron™ utilizes hardware-based identity verification and continuous authentication.
-
05
NetTron™ is embedded with its own quantum-resistant cryptographic engine, with distributed self‑key generation and key rotation across nodes.
-
06
NetTron™ extends secure, encrypted communications directly to each protected asset or site (ATM, hospital device, drone, etc.) without relying on centralized MDM platforms.
Unified Security Control
NetTron™ Access
Management Dashboard
What your current individual cybersecurity vendors deliver separately, NetTron™ fundamentally converges firewalls, VPNs, NAC, ZTNA, MDM, and PQC into one hardware-secured, quantum-resilient, self-managing network fabric.
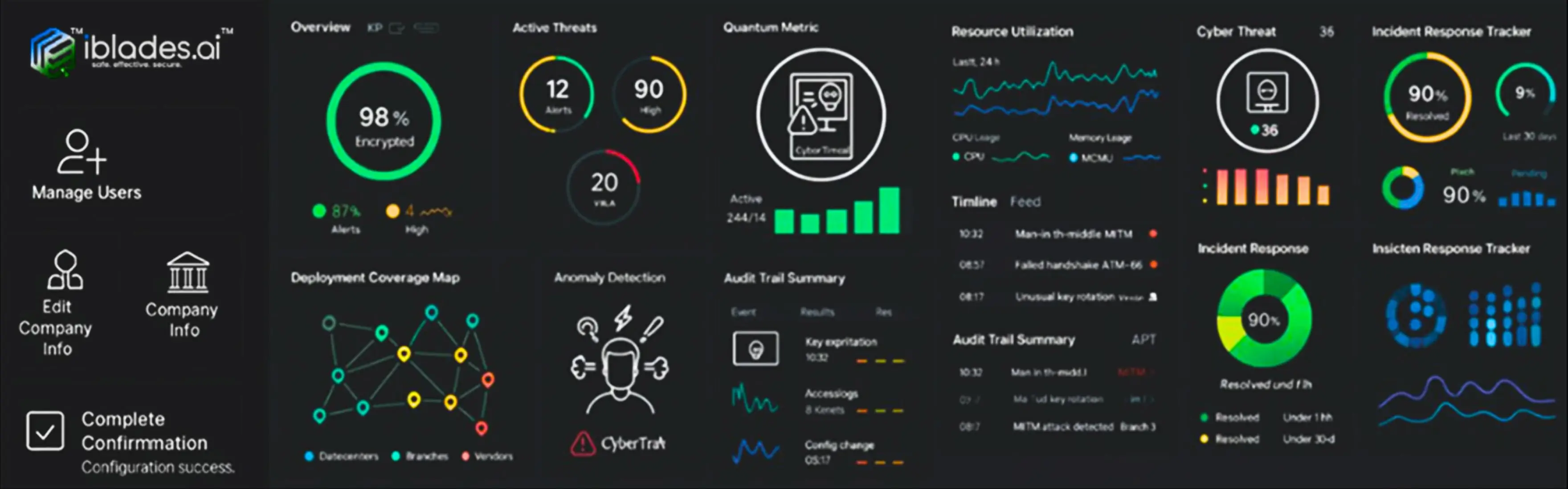
Instant Edge Protection
NetTron™ Suite
- Perimeter Firewalls
- Next-Gen Firewalls
- VPN and Remote Access Gateways
- Mobile Device Management
- Network Access Control
- Zero Trust Network Access
- Quantum Cryptography
- Remote Asset Access
- Secure Access Service Edge (SASE)

Why Choose NetTron™
NetTron™ Suite
Exposed and VulnerableCompetitor / Category
-
Palo Alto Networks (Perimeter & Next-Gen Firewalls)
-
Cisco (VPN and Remote Access Gateways)
-
Microsoft Intune (Mobile Device Management)
-
Aruba (HPE ClearPass – Network Access Control)
-
Okta (Zero Trust Network Access)
-
SandboxAQ (Quantum Cryptography / PQC)
-
BlackBerry (UEM / Cylance – Remote Asset Access)
-
Zscaler (SASE – Secure Access Service Edge)
How NetTron™ + GuardTron™ Replaces Them
-
NetTron™ integrates edge firewalls directly into hardware nodes at each site, eliminating the need for standalone firewall appliances.
-
GuardTron™ applies zero-trust segmentation and quantum-safe encryption between all edges.
-
NetTron™ nodes create encrypted tunnels automatically between authorized assets using GuardTron™ quantum-resilient keys.
-
GuardTron™ embeds device authentication and policy enforcement directly at the hardware layer of each node or StealthCase™.
-
GuardTron™ integrates identity-based access into the network layer itself, with each NetTron™ node acting as a self-attesting, cryptographically validated access point.
-
GuardTron™ replaces this with hardware-based identity verification and continuous authentication, built into each NetTron™ edge device.
-
GuardTron™ uses its own embedded quantum-resistant cryptography engine, with distributed self-key generation and key rotation across nodes.
-
NetTron™ extends secure, encrypted communications directly to each protected asset or site (ATM, hospital device, drone, etc.) without relying on centralized MDM platforms.
-
NetTron™ and GuardTron™ deliver SASE functionality locally at each node, creating self-contained micro-clouds for secure access and data exchange.
Built for the Real World
Mission-ready applications
Financial Institutions:
GuardTron™ enables banks and financial organizations to achieve up to 50% savings while upgrading and simplifying their cybersecurity posture. It protects their edge networks and ensures compliance with quantum-computing-ready regulations, including SEC, Dodd-Frank, Sarbanes- Oxley, and FINRA.
Healthcare Providers and Medical Companies:
GuardTron™ helps hospitals and healthcare organizations upgrade their cybersecurity protection with up to 50% savings, meeting existing and emerging mandates such as HIPAA, DPRS, and CCPA, while defending against ransomware and network vulnerabilities.

Infrastructure Providers:
GuardTron™ safeguards critical infrastructure assets such as power grids, water treatment facilities, emergency services, and municipal networks—ensuring these essential systems remain protected from ransomware, data breaches, and malicious actors.
Government and Military Agencies:
GuardTron™ provides mission-grade security for classified networks, field operations, and critical infrastructure, ensuring encrypted communications and operational integrity even in contested or disconnected environments.
Inside the Technology
How GuardTron™ Does it
GuardTron™ II (plug-and-play edge appliance) adds a new layer in your cyber advisory stack—enabling you to deliver NIST-approved, quantum-ready, autonomous edge security to government and enterprise clients without adding headcount or complexity.
Leak-Proof Mobility:
Real-time encryption keeps your team secure anywhere, anytime — no matter the network or device.

Regulatory Compliance:
Effortlessly meet stringent cybersecurity mandates with built‑in encryption, auditing, and access controls.
Operational Efficiency:
Simplify and secure your infrastructure with a single interoperable platform — eliminating tool sprawl and vendor overlap. AI/ML-Driven Defense: Proactively prevent data breaches and downtime with intelligent, self-learning threat detection.
Quantum-Ready Security:
Stay ahead of emerging quantum threats with post-quantum encryption and future-proof key management.
Edge-to-Cloud Protection:
Extend zero-trust security from local endpoints to cloud
applications for continuous, end‑to‑end defense.
Cost Savings:
Cut cybersecurity spending by up to 50% while boosting protection and scalability
- Data Centers
- Branches
- Vendors
Global Secure Coverage
GuardTron™ Deployment Coverage Map
Peer-to-Peer Anonymized Network Ensures World’s First NIST-Approved, End-to-End, Untraceable Communication to Maximize Privacy and Security for Both Parties.
Your Phone is the Target
Certified Retransmission a la carte Cyber Security
Secure Comms for Modern Mobility
Experience the next generation of secure mobility with the ManoTron™ line of RadioZero™ and Cyber™ Cases – Supported by NetTron™ Lite – A hardware-anchored platform that transforms any smartphone into a certified retransmission endpoint for protected government, defense and enterprise communications.
Product Comparison Overview
Naked Phone vs RadioZero™
vs Cyber vs Cyber Plus
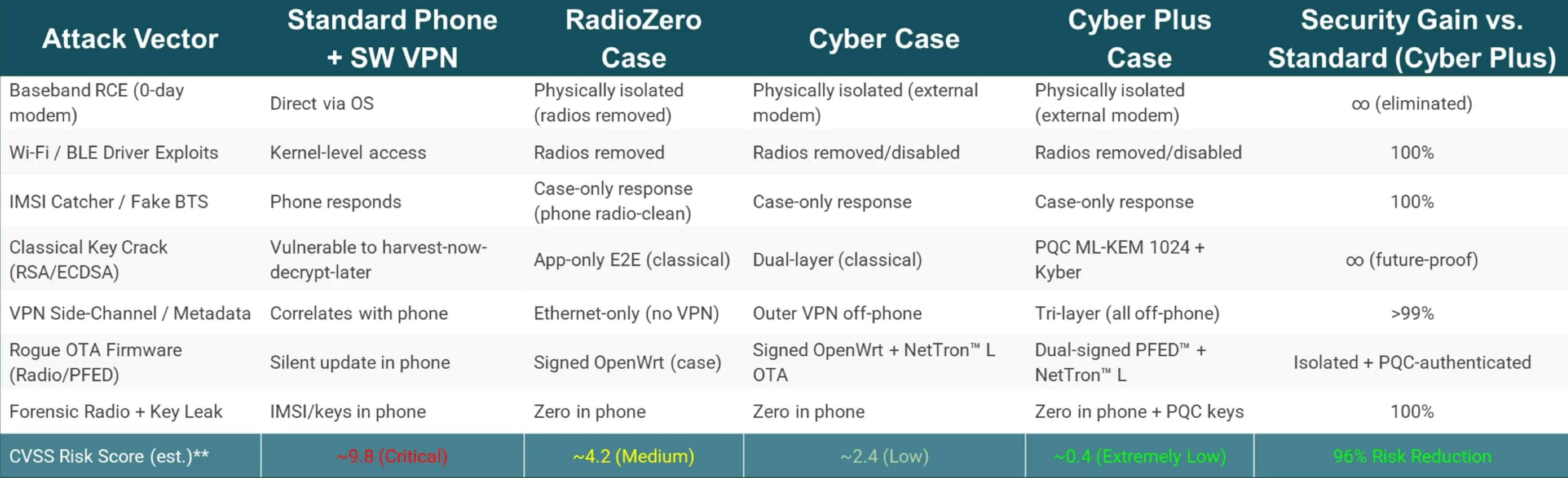
Why It’s Unbreakable
Key Security Advantages
World’s First Peer-To-Peer NIST Quantum
Ready Cyber Secure Edge Device
Dual-Layer Encryption — Built‑In
-
ManoTron™ enforces two independent layers of encryption into full alignment with NIST retransmission requirements.
-
The outer layer, NetTron™ Lite automatically establishes a VPN to an authorized grey- network gateway.
-
The inner layer (QTRON™ app on the phone) provides end-to-end session encryption for calls, messages, and data.
-
No traffic passes outside these tunnels — ensuring all communication is protected before leaving the device.
Baseband and Data Isolation
-
Physical separation between the phone’s USB data interface and the embedded LTE modem provides complete protection from direct baseband exposure.
-
The bridge controller and routing firewall eliminate any shared path between user data and radio interfaces, preventing lateral access or cross-domain leaks.
Trusted From Boot to Update
Secure Firmware Lifecycle
Each StealthCase™ runs a signed OpenWrt image with secure-boot validation, vendor-vetted release pipeline, and controlled OTA deployment through NetTron™ Lite or enterprise MDM.
Every firmware update is cryptographically authenticated and logged, ensuring full traceability and eliminating the risk of rogue firmware.

All non-networking services — Wi-Fi, Bluetooth, NFC, and local debug interfaces — are physically removed or disabled.
NetTron™ Lite operates as a single-purpose retransmission bridge, with locked U-Boot recovery, HTTPS-only management, and strict role-based access control.
Intelligent sleep-mode management keeps power draw under 400 mA average and below 20 % phone-battery impact during normal use.
The device wakes automatically on LTE ring events, optimizing efficiency without compromising readiness.

Built for the Field
Tactical Encryption for High-Risk Operations
ManoTron™ Cyber Retransmission™ ensures secure, reliable communications for assets operating in high-risk environments. Whether conducting covert operations in hostile territories, coordinating disaster response in remote areas, or maintaining discretion during sensitive corporate or governmental missions, this tactical SecureComm device keeps your data safe.
Its external retransmission hardware isolates your smart device from network threats, enabling encrypted voice and data transmission without compromising your position. Trusted by military units, intelligence operatives, government agencies, and corporate safety teams, this Secure Relay System delivers mission-critical connectivity when it matters most.
Inside the System
How ManoTron™ Cyber Retransmission™ Case Does It
-
01 USB-C Tether Only classes.
Enumerates as Ethernet (CDC-ECM); no mass-storage or ADB
-
02 LTE / 5G Connectivity future
Global LTE + sub-6 GHz 5G (bands n1, n3, n5, n7, n28, n77 /
n78 / n79); mmWave ready -
03 Two-Layer Encryption
Outer NetTron™ Lite VPN + inner QTRONTM EUD tunnel
-
04 Grey-Network Management
Updates and diagnostics restricted to authenticated VPN channel
-
05 Role-Based Access
Separate user / admin credentials via LuCI + SSH.
-
06 Persistent Logging VPN
Syslog-NG local retention + optional remote forwarding over
-
07 Supply-Chain Assurance
Components sourced from ISO 20243-certified vendors
-
08 Form-Factor Adaptability
Modular chassis for Samsung S23/S24/S25 series and future devices
Stronger in the Field
Operational Benefits
Zero user configuration
Power on, plug in, and the VPN stack initializes automatically.
Cross-region
Readiness supports North America, EMEA, and APAC LTE/5G bands.
Self-healing network
NetTron™ Lite monitoring and automated reconnection routines.
Quantum-resilient foundation
Ready for PQC (post-quantum crypto) upgrade path.
Use Cases
Government and defense retransmission nodes.
Healthcare or financial data isolation gateways.
Secure mobile communications for field teams.
Edge-of-network classified or controlled-unclassified data transfer.
